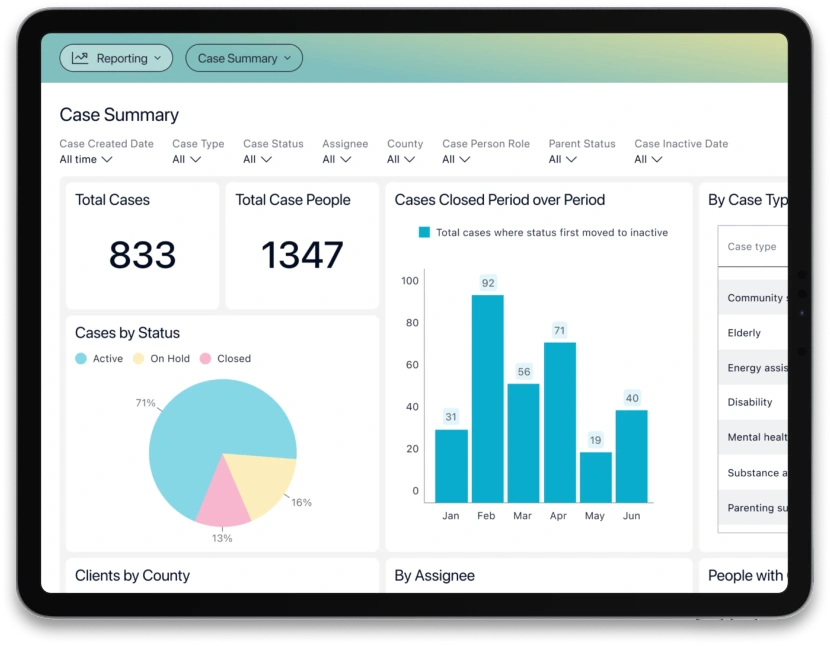
Casebook is leading human services software, offering a configurable platform that has you covered from intake through reporting.































Managing data should impact your community more than your pockets. Casebook’s per-user-pricing model and flexible plans allows you to select the number of users that make sense for your organization.